Next Gen Managed Detection & Response Services
Redefining Your Cyber Security Outcomes
1 Minute
10 Minutes
45 Minutes
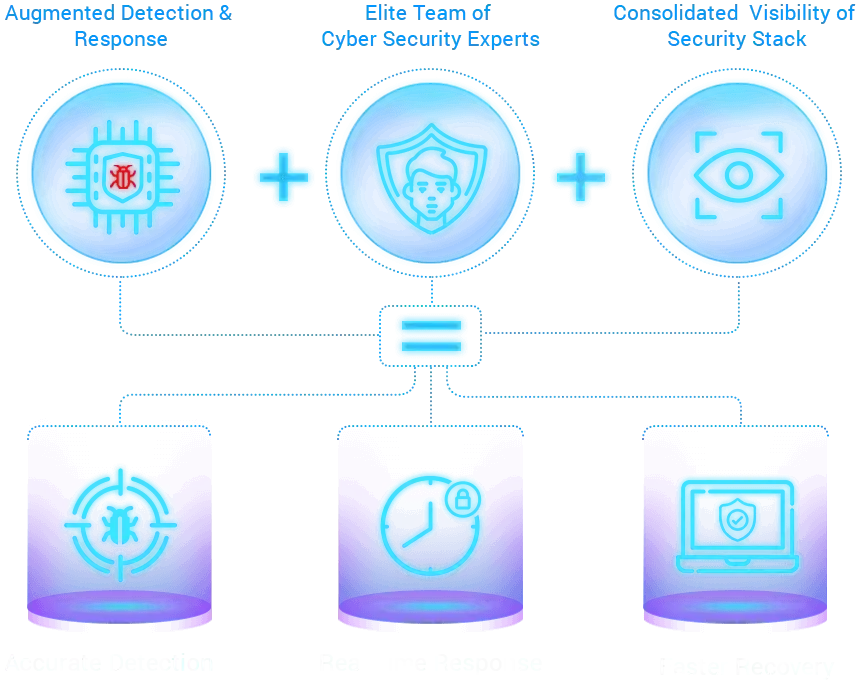
Our Capabilities
Holistic Protection Suite to Safeguard your Digital Assets from Modern Day Threats

Managed Detection & Response
360-degree robust protection for users, network, cloud, IoT and mobility
Read More
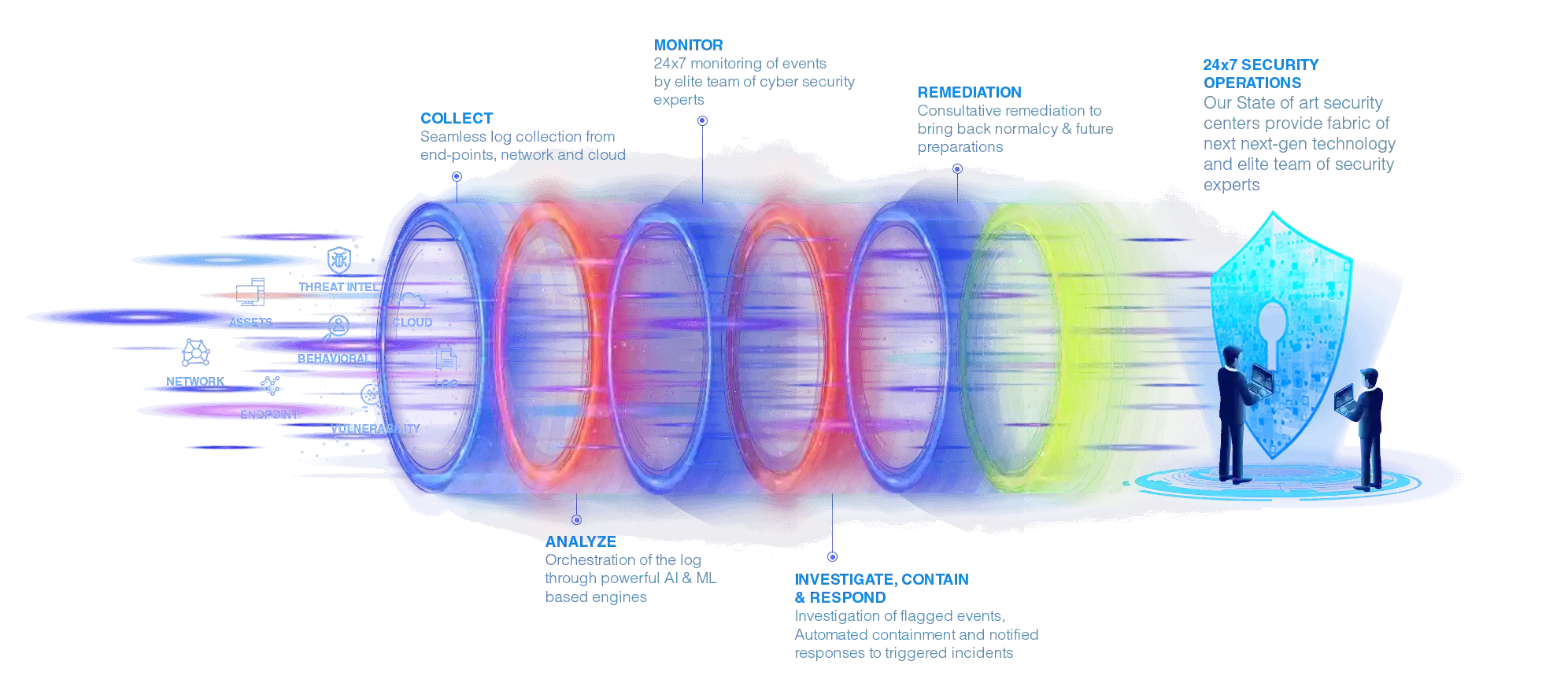
Cyber Security Operation Centre
24/7 security operations to provide seamless protection from known and unknown cyber threats
Read More
Governance, Risk Management & Compliance
We review security policies, technical compliance & cyber risk management posture to mitigate risk and remediate
Read More
Vulnerability Assessment & Penetration Testing
Our vulnerability assessment & testing service defines, identifies, prioritizes vulnerabilities and test them in a controlled environment
Read More