HOW IT WORKS
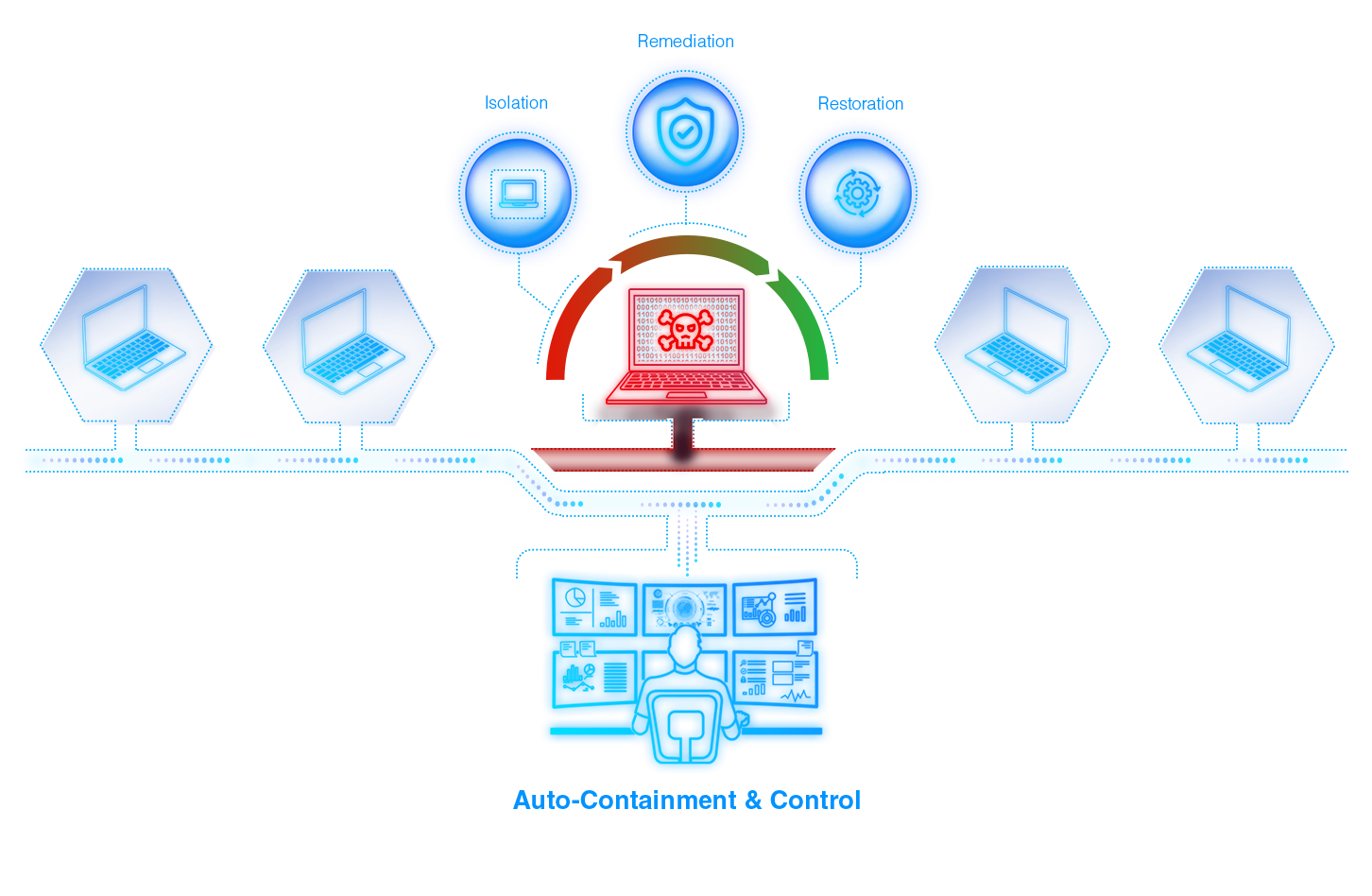

Automated Isolation of Affected Entities Prevents Advancement Of Threat Vector and Controls The Damage
An Intelligent Technique to Stop Lateral Movement of Malware and Threat Carriers
Our AI-powered auto isolation feature disconnects the affected entity from the rest of the network and prevents the further spread of the threat and minimizes the damage.
The affected system is sent to a sandbox environment and is being diagnosed for the problem in a secure environment. The sandbox zone is used to determine the type of vulnerability and possible solution.
Though the affected sytems are isolated from the internal network, the support control system provides privileged access to a security analyst for investigation and recovery.
The checked and remediated entity is restored back to its original network and available for use without any intervention of the local IT team.
Reduced burden on cyber security and IT teams
Automation provides real-time blocker to control damage
Prevention of collateral damage and eduction in business and financial loss
Seamless availability of containment and restoration system without human intervention

Blog

Do you ever wonder about the pre-built software in your computer? What will happen if it affects your security? What is the worst-case scenario? A pre-installed piece in your computer can pose a serious security risk [...]
Read MoreBlog

Citrix Systems, Inc. is an American multinational software company that provides server, application & desktop virtualization, networking, software as a service (SaaS), and cloud computing technologies [...]
Read MoreBlog

Technology is constantly evolving, and so is its relevance. In today’s world, its increasingly difficult to imagine a day without technology. Just think of the number of times that you rely on new age technologies for each activity [...]
Read More