HOW IT WORKS
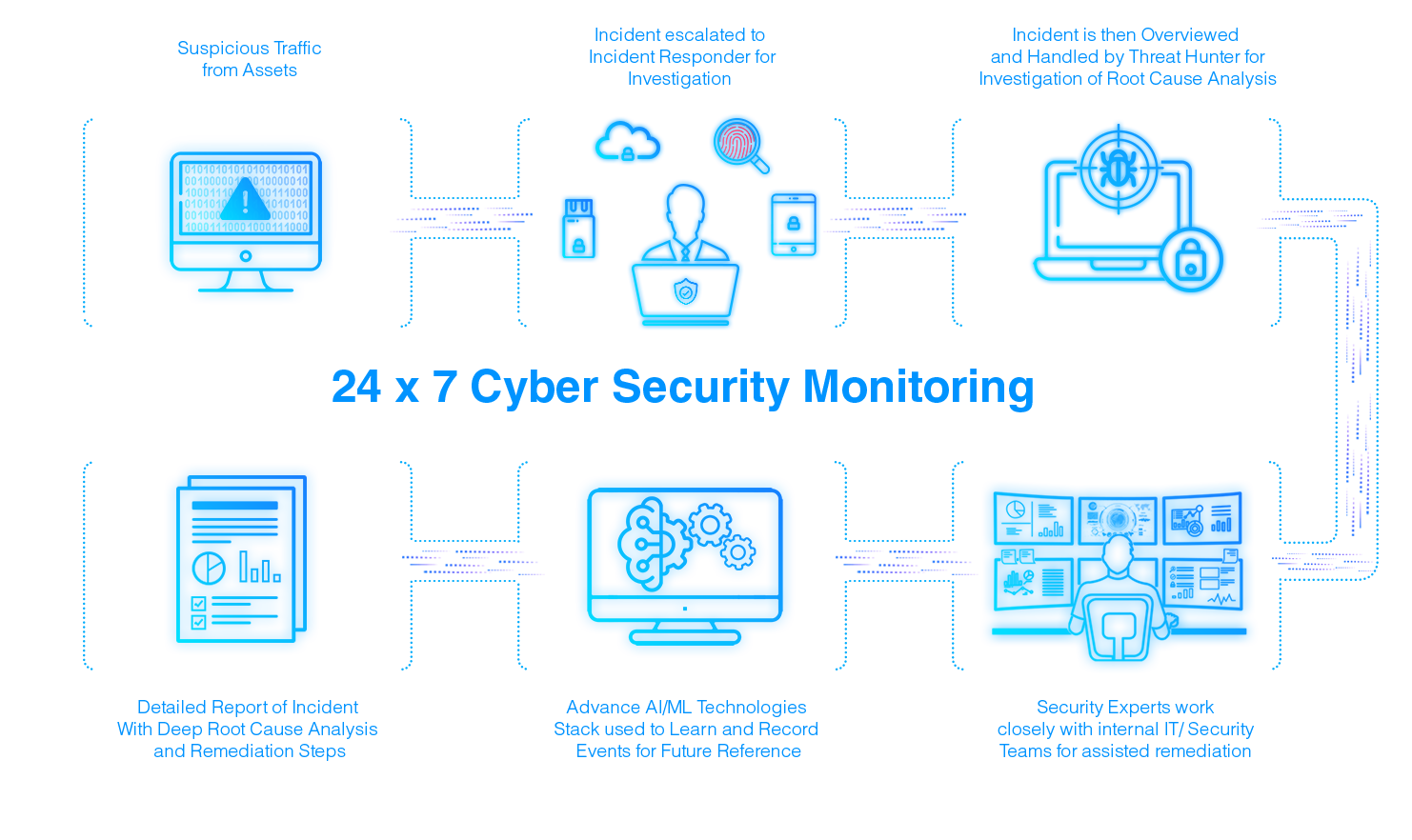

Leveraging Advanced Technologies & Techniques To Gain Visibility, Security & Control
Our Intelligence Monitoring System ensures that Advanced Threats and Attacks are Identified and Thwarted before Damage is done
Our elite team of security experts monitors the entire security ecosystem to detect and respond to new-age malware and sophisticated attack methods. This helps to counter and stop the breaches before the damage is done.
Our Intrusion Detection & Prevention System monitoring protects against network and application-level attacks, provides protection against intrusion attempts, malware, ransomware, and DDoS attacks. It detects and blocks backdoor activity and stops the horizontal spread of the threat vector.
The perimeter security requires extra vigilance as it is designed to protect the entry point of most of the threats and attacks. Our network monitoring process is designed to give extra protection to perimeter devices like firewalls, routers, and access points.
We use the information repository and use advanced techniques to monitor various log categories like syslogs, operating system logs, and archives. The AI-enabled correlation is used to gain more intelligence and ensures protection from external and internal threats.
Firewalls are very important appliances and designed to provide the first line of defense. We monitor the firewall traffic to stop malware and attacks right at the entry points to prevent any damage to the internal network.
Our cyber security monitoring team provides periodic reports on overall security activities customized for executive and technical teams. We work with the internal IT team of the customer to further strengthen the security posture.
Round the clock protection against malware, trojans, and targeted attacks
Enhanced visibility and control over the entire cyber security ecosystem
Rapid and accurate response to curated attacks before the damage is done
Improved cyber security posture and risk profile due to continuous vigilance
Drastic reduction in downtime which can result in significant financial & business loss
Improvement in future strategies and business continuity plans

Blog

Do you ever wonder about the pre-built software in your computer? What will happen if it affects your security? What is the worst-case scenario? A pre-installed piece in your computer can pose a serious security risk [...]
Read MoreBlog

Citrix Systems, Inc. is an American multinational software company that provides server, application & desktop virtualization, networking, software as a service (SaaS), and cloud computing technologies [...]
Read MoreBlog

Technology is constantly evolving, and so is its relevance. In today’s world, its increasingly difficult to imagine a day without technology. Just think of the number of times that you rely on new age technologies for each activity [...]
Read More