HOW IT WORKS
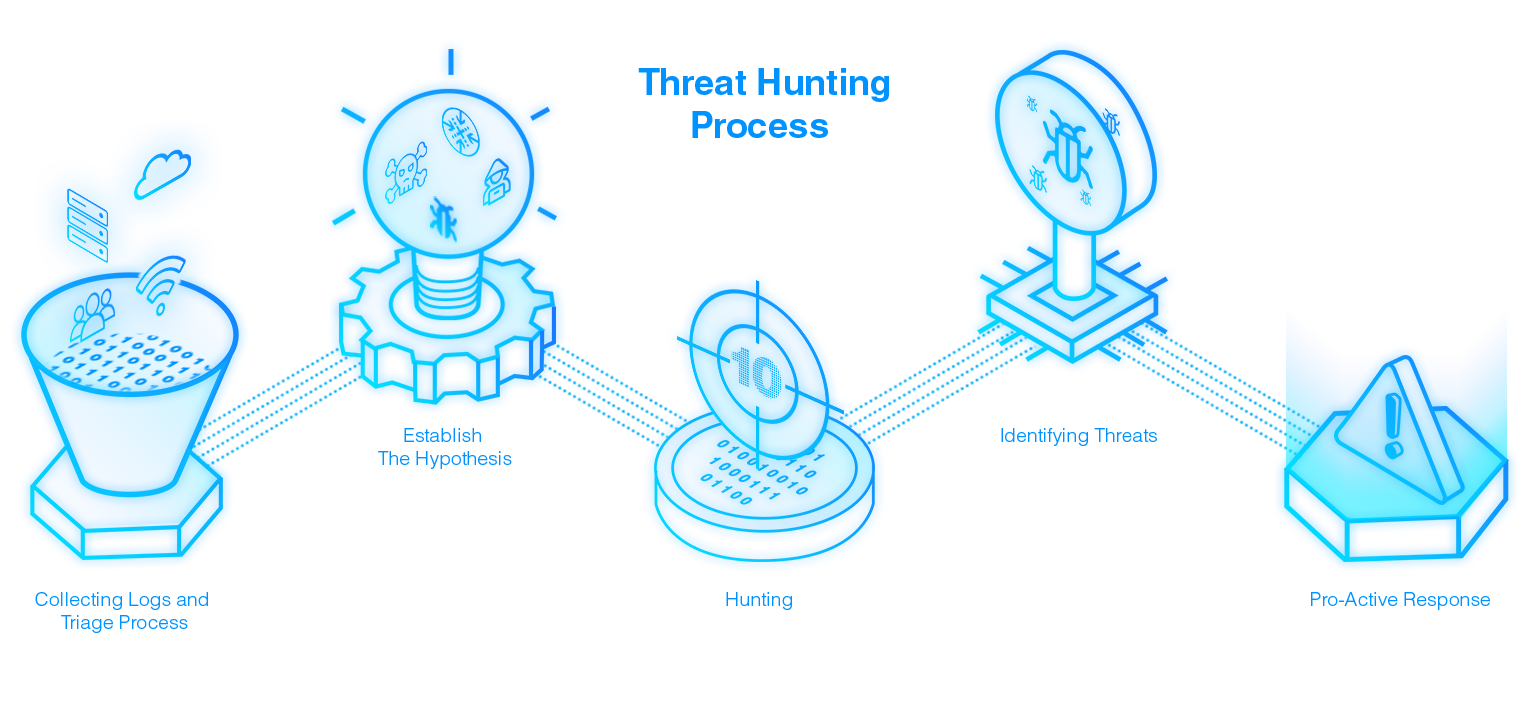

Our Security Experts use Machine-Aided and Manual Techniques to Proactively search Hidden Threats
Elite Team of Security Experts looks out for Hidden Threats to Provide Proactive Protection against Sophisticated Threats
Our elite team cyber security experts look for threats originating from the internal ecosystem using AI-based systems and manual techniques to search compromised systems, processes and altered user behavior. The integration with advanced UEBA engines refines the process and gives advanced protection.
A collaborative platform of network threat analytics, user behavior analysis, end-point, and application analysis provides a complete report and actionable items and improves overall cyber security strategy.
Our threat hunting services integrated the operation strategy of security analysts and threat hunters to build a unified threat profile. The concerted approach helps in the faster and accurate investigation and root cause analysis.
Our threat hunting team is equipped with advanced Machine Learning and intelligent tools which help them proactively hunt the threats from internal and external environments and use the data model to find solutions.
The logs collected from various sources like firewalls, SIEM, and more are further enriched with advanced search tools and to help the threat hunting team.
Our threat hunting process leverages on AI & ML tools to automate event analysis, factor identification, and response timelines to automate the threat hunting process. This enables faster and accurate threat hunting.
A proactive approach to uncover hidden malware to define and design a future-ready security framework
Improved incident response time with forecasted impact analysis and mitigation plan
Appropriate mitigation of threats with an improved defense system which can predict the possibility of a breach
Evolving to next-generation security operations process with intuitive intelligence
Reduction in false positives and improvement in efficiency
Reduces damage and overall risk to the organization by providing proactive alerts

Blog

Do you ever wonder about the pre-built software in your computer? What will happen if it affects your security? What is the worst-case scenario? A pre-installed piece in your computer can pose a serious security risk [...]
Read MoreBlog

Citrix Systems, Inc. is an American multinational software company that provides server, application & desktop virtualization, networking, software as a service (SaaS), and cloud computing technologies [...]
Read MoreBlog

Technology is constantly evolving, and so is its relevance. In today’s world, its increasingly difficult to imagine a day without technology. Just think of the number of times that you rely on new age technologies for each activity [...]
Read More