HOW IT WORKS
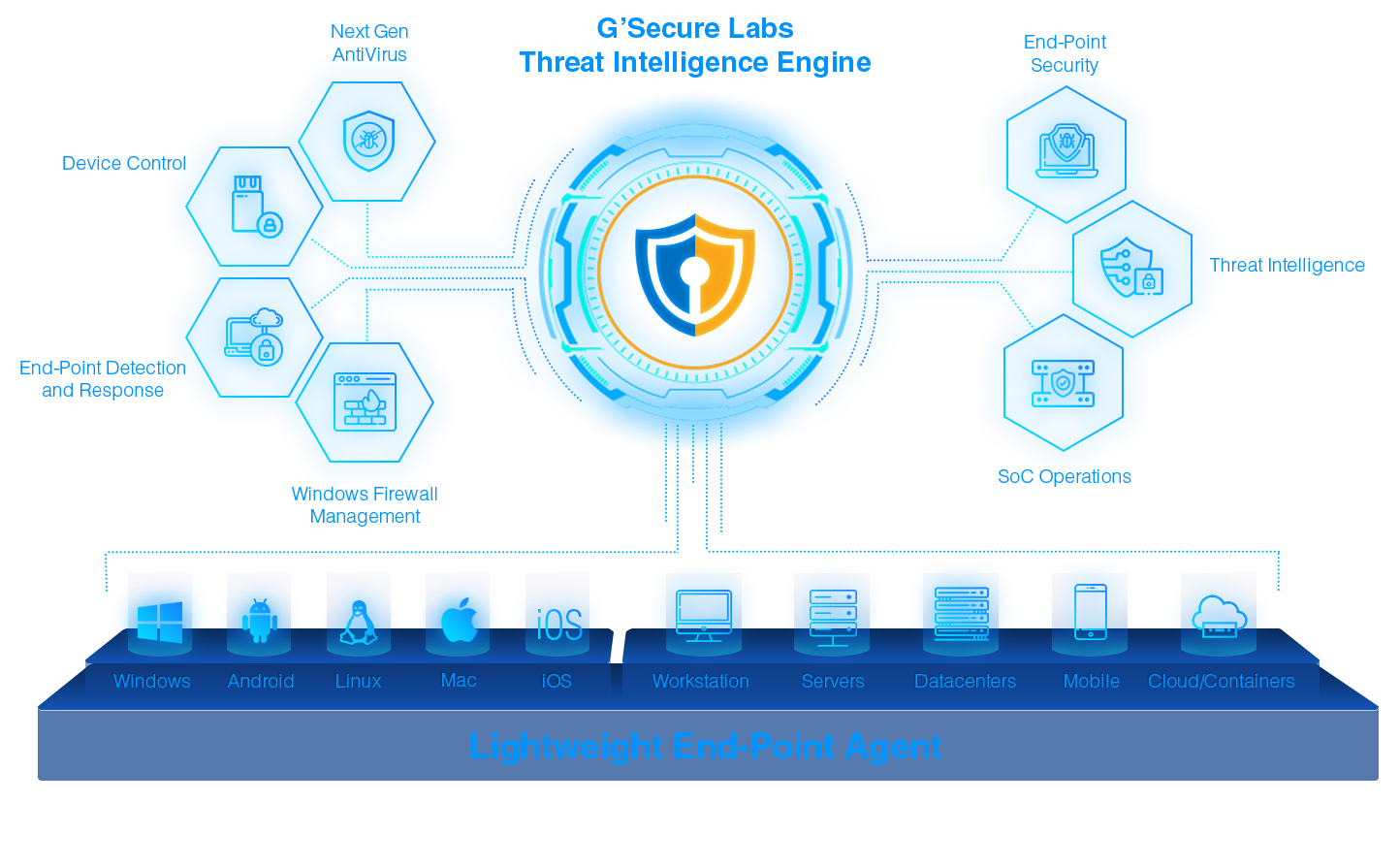

Intelligent Protection for End-Points and Servers to Protect them from Malware & Zero-Day Attacks
Holistic Protection Suite to Safeguard your Digital Assets from Modern-Day Threats
Protects against the entire spectrum without requiring daily and cumbersome updates. It combines the best prevention technologies — Machine Learning, AI, indicators of attack (IOAs), exploit blocking and more to stop ransomware and malware-free and file-less attacks and covers the gaps left by legacy AV and fully protects endpoints online and offline.
Enables you to fully understand the threats in your environment and easily prioritize responses with threat severity assessment. It eliminates guesswork so you can respond to threats decisively. It automatically determines the scope and impact of threats found in your environment.
Unravels an entire attack in one easy-to-grasp process tree enriched with contextual and threat intelligence data. It provides an unparalleled alert context and visibility and keeps detection details for 90 days.
Provides powerful response action to contain and investigate compromised systems. It ensures on-the-fly remote endpoint access for immediate action with surgical precision.
Makes it easy to create, manage and enforce policies It defends against network threats and provides instant visibility to enhance protection and inform action.
Provides detailed visibility on USB device usage. It enables granular policy enforcement to ensure control over USB devices used in the environment.
Best in class End-Point Detection & Response product
AI-based signature-less detection through a light weight agent
Global Threat Graph access for forensics and breach analysis
Best-in-class protection from modern cyber-attacks and intrusions viz. zero-day attacks, targeted attacks, file-less malware, etc.
Intelligent feeds of over 1 trillion events per week and analytics through Machine Learning
Based on Indicators of Attack (IOA) & Indicators of compromise to prevent targeted attacks
Remediation schedule for rogue nodes along with target footprint analysis
Advance Threat Graph feeds for end-points and servers

Blog

Do you ever wonder about the pre-built software in your computer? What will happen if it affects your security? What is the worst-case scenario? A pre-installed piece in your computer can pose a serious security risk [...]
Read MoreBlog

Citrix Systems, Inc. is an American multinational software company that provides server, application & desktop virtualization, networking, software as a service (SaaS), and cloud computing technologies [...]
Read MoreBlog

Technology is constantly evolving, and so is its relevance. In today’s world, its increasingly difficult to imagine a day without technology. Just think of the number of times that you rely on new age technologies for each activity [...]
Read More