HOW IT WORKS
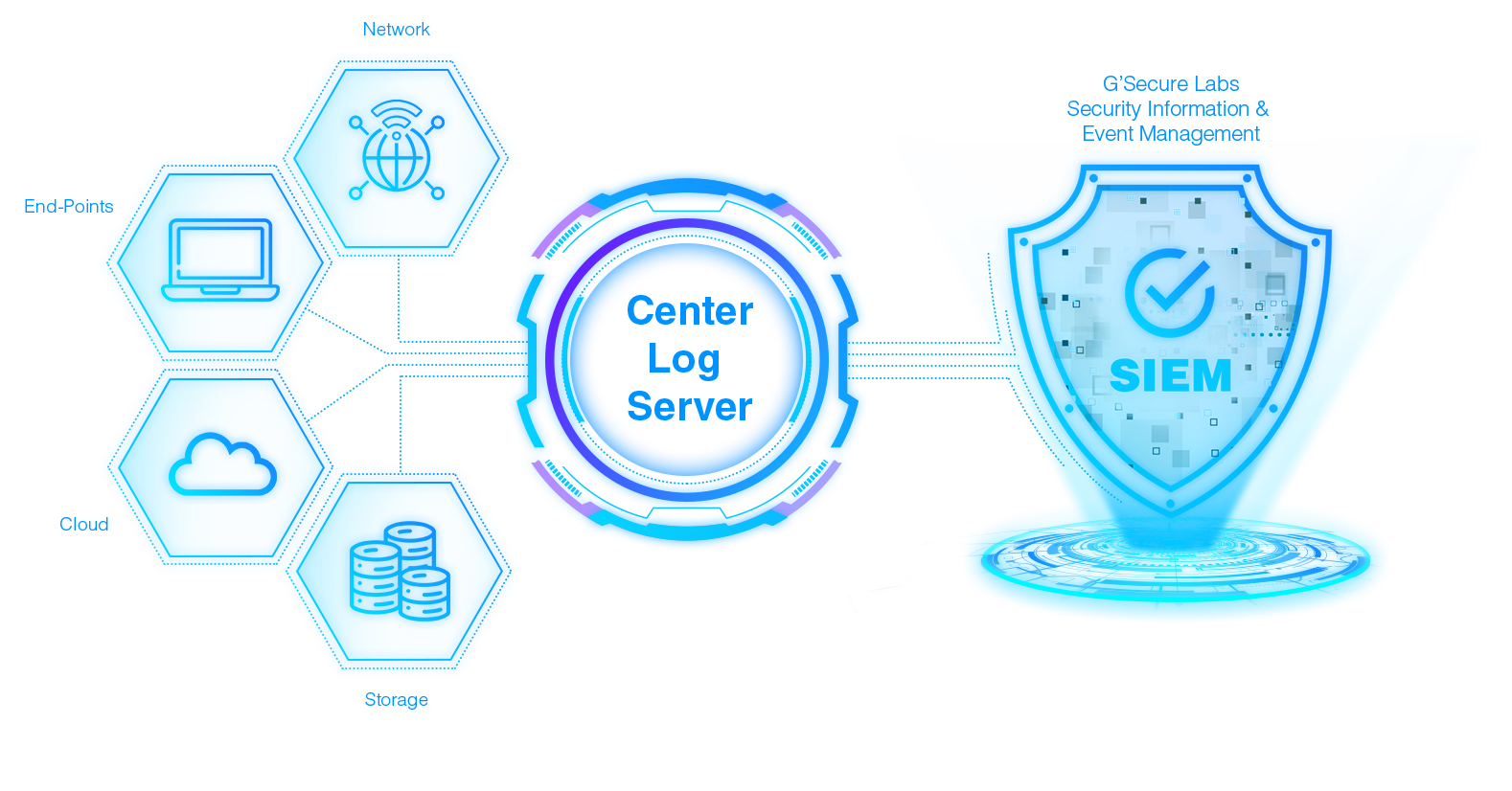

Our Powerful & Intelligent SIEM Collects, Analyzes, Correlates Information from Digital Assets, Cloud & Network to Create Actionable Intelligence for Robust Protection
A Flexible and Cost-Effective Solution for Collection, Analysis, Correlation & Orchestration of Logs & Events
The qualitative intelligence supports in IOC/IOA gathering and verification with curated feeds from the dark web, deep web, and surface web, results in reduced the research time for analysis of events. Our AI and ML algorithms provide insights on correlated cases and support proactive planning.
Out of the box dynamic playbooks automate the initial monotonous actions required in known cases and increases the efficiency of response and remediation process resulting in increased productivity of security operations.
Based on the past trends of alerts G’SIEM predicts probable threats that can be seen during the upcoming week. Accordingly, SOC resources can be utilized efficiently. This strengthens the approach of proactive security and provides an extra layer of security.
Our inbuilt knowledge base of Blacklisted IPs, Blacklisted domains, critical assets, phishing domains, and custom knowledge bases can be created on the go. With every case, we associate a list of steps tailored for a particular type of alert. Hence, it is ensured that all the necessary steps are followed and no actions are missed.
The Bulk Action feature helps in handling the multiple False Positives or redundant cases during an outbreak in an effective manner. It is integrated with MITRE and NIST frameworks, which help in understanding the adversary tactics and techniques.
Our log retention options are designed to provide flexibility as per your business and statutory requirements.
Enhanced productivity in cyber security operations
Complete visibility of events from assets, cloud & network
Curated Intelligence forensics and breach analysis
Continuous improvement of security posture and policies
Risk mitigation and compliance with business and statutory regulations
Log retention for forensics and root cause analysis

Blog

Do you ever wonder about the pre-built software in your computer? What will happen if it affects your security? What is the worst-case scenario? A pre-installed piece in your computer can pose a serious security risk [...]
Read MoreBlog

Citrix Systems, Inc. is an American multinational software company that provides server, application & desktop virtualization, networking, software as a service (SaaS), and cloud computing technologies [...]
Read MoreBlog

Technology is constantly evolving, and so is its relevance. In today’s world, its increasingly difficult to imagine a day without technology. Just think of the number of times that you rely on new age technologies for each activity [...]
Read More