HOW IT WORKS
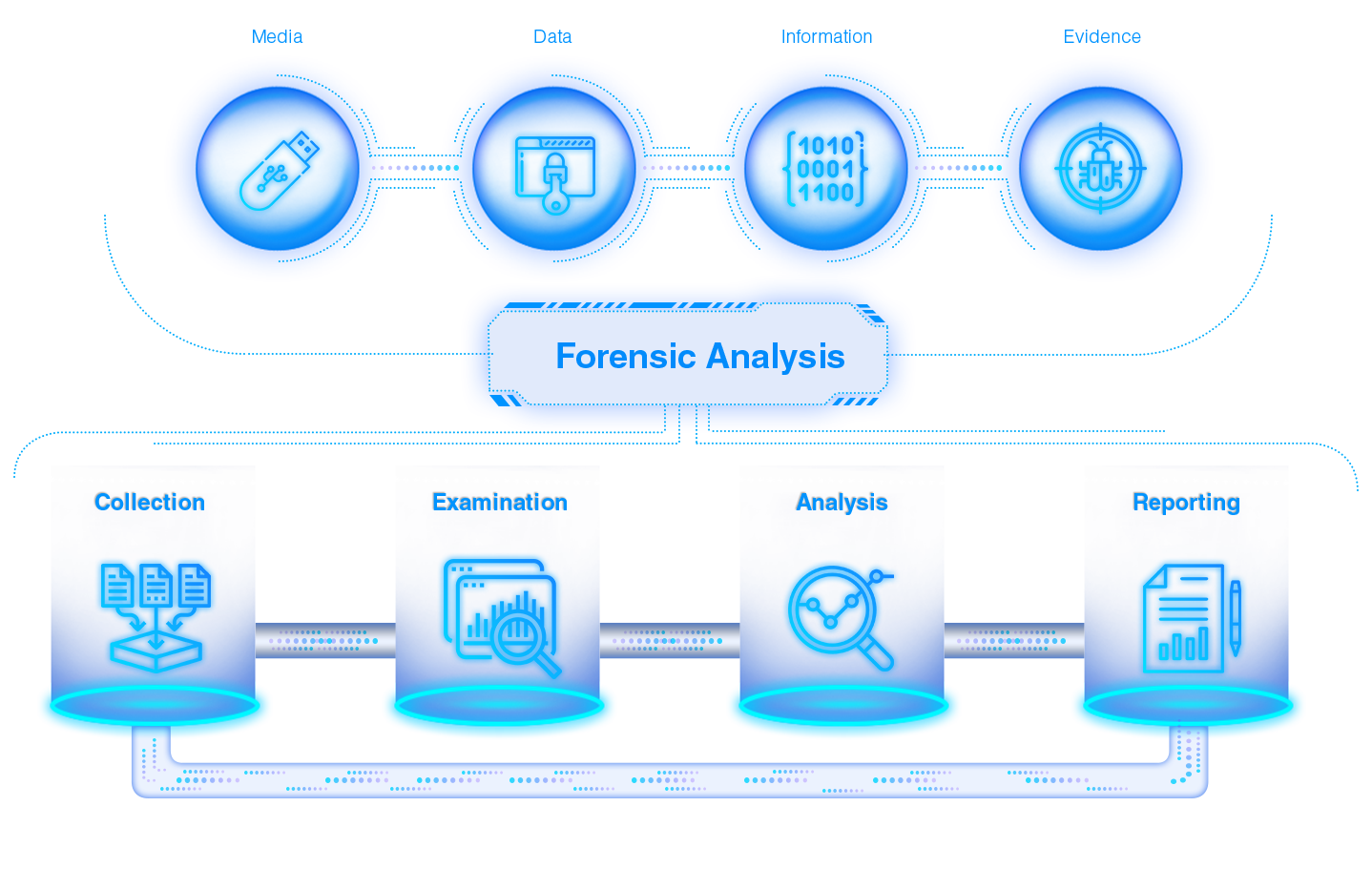

A Methodological Approach to Detect, Harvest & Analyze Cyber Security Breach Evidences for Future Protection
Elite Cyber Forensics Services to recover Hidden & Encrypted Information related to a Cyber Security Breach
Our expert team of cyber security forensics analyzes the source, motive and impact, and remediation of a cyber security breach. The bespoke approach of industry-specific techniques helps to re-organize cyber security policies to counter similar attacks.
The process of an extensive investigation of connected IOC/IOA of specific incidents helps to determine the root cause and helps to build playbooks for future response and automation.
Advance Persistent Threats (APT) are targeted attacks for specific motives. Our team of analysts studies the pattern of such attacks and builds a model report to protect against targeted attacks.
In case of a breach, it is a smart idea to look into old records for correlation. Our log analysis team uses advanced search systems to look into old archived logs and find a correlation to reach the root of the problem which allowed the breach.
Deep understanding of security procedures and policy improvement requirements
Helps to combat attacks and infiltrations of similar nature and reduces redundant steps
Improvisation in risk mitigation plans and impact analysis models
Helps to comply with regulations and law enforcements directives

Blog

Do you ever wonder about the pre-built software in your computer? What will happen if it affects your security? What is the worst-case scenario? A pre-installed piece in your computer can pose a serious security risk [...]
Read MoreBlog

Citrix Systems, Inc. is an American multinational software company that provides server, application & desktop virtualization, networking, software as a service (SaaS), and cloud computing technologies [...]
Read MoreBlog

Technology is constantly evolving, and so is its relevance. In today’s world, its increasingly difficult to imagine a day without technology. Just think of the number of times that you rely on new age technologies for each activity [...]
Read More