Managing Risk & Compliance
With a Holistic View of your Organization’s Security Policies, Technical Compliance & Cyber Risk Management Posture we Assess and Report the loopholes to Fix and Remediate
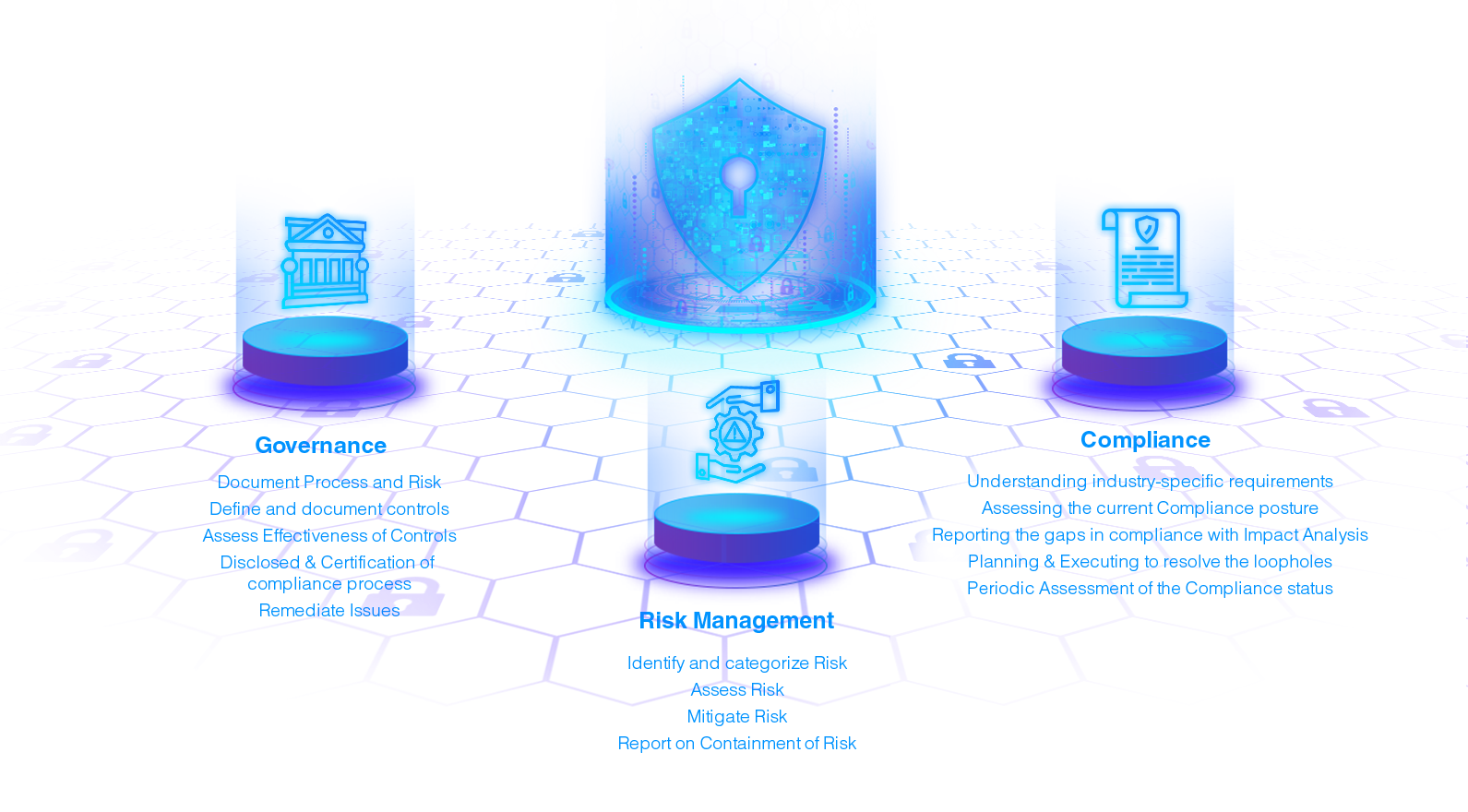

Our Bespoke Audit and Compliance services ensure that your Organization remains Compliant to Global Data Protection and Cyber Security Frameworks such as GDPR, HIPAA, NIST, SANS, ISACA, and beyond
With a Holistic View of your Organization’s Security Policies, Technical Compliance & Cyber Risk Management Posture we Assess and Report the loopholes to Fix and Remediate

A Complete Solution Suite to Cover your Regulatory Needs
Periodic audit ensures that the organization remains safe. Our audit services follow international audit practice standards for complete or on-demand audit.
Our consultative approach to attain compliance with industry specific frameworks, guidelines and standards mitigates the risk of actions from agencies.
We understand your reputation is important, we help you to fix issues in operational, technical, regulatory policies and mitigates risks of cyber frauds and data compromise.
We help you to automate your risk assessment services to analyze, prevent and assess any potential risk factor with agility.
GRC gives resolution to immediate and long-term risk exposure and allows an agile and scalable control on the digital ecosystem.
GRC helps reduce costs in maintaining redundant controls, tests, issues, actions, and reporting across departments, thus giving a better ROI.
GRC gives clarity to stakeholders regarding processes, functions and overall transparency to visibility to strengthen trust factors.
Solidifies brand recognition in the market as compliance with regulatory requirements and proactive risk management attracts customers and suppliers.
Automation keeps you audit-ready and ensures policies and compliance checks are in place to face any audit even on short notices.
Increases ROI on security investments as fixing the compliance issues and adherence to standards reduce chances of penalty or action.
Blog

Citrix Systems, Inc. is an American multinational software company that provides server, application & desktop virtualization, networking, software as a service (SaaS), and cloud computing technologies [...]
Read MoreBlog

Do you ever wonder about the pre-built software in your computer? What will happen if it affects your security? What is the worst-case scenario? A pre-installed piece in your computer can pose a serious security risk [...]
Read MoreBlog

Technology is constantly evolving, and so is its relevance. In today’s world, its increasingly difficult to imagine a day without technology. Just think of the number of times that you rely on new age technologies for each activity [...]
Read More