HOW IT WORKS
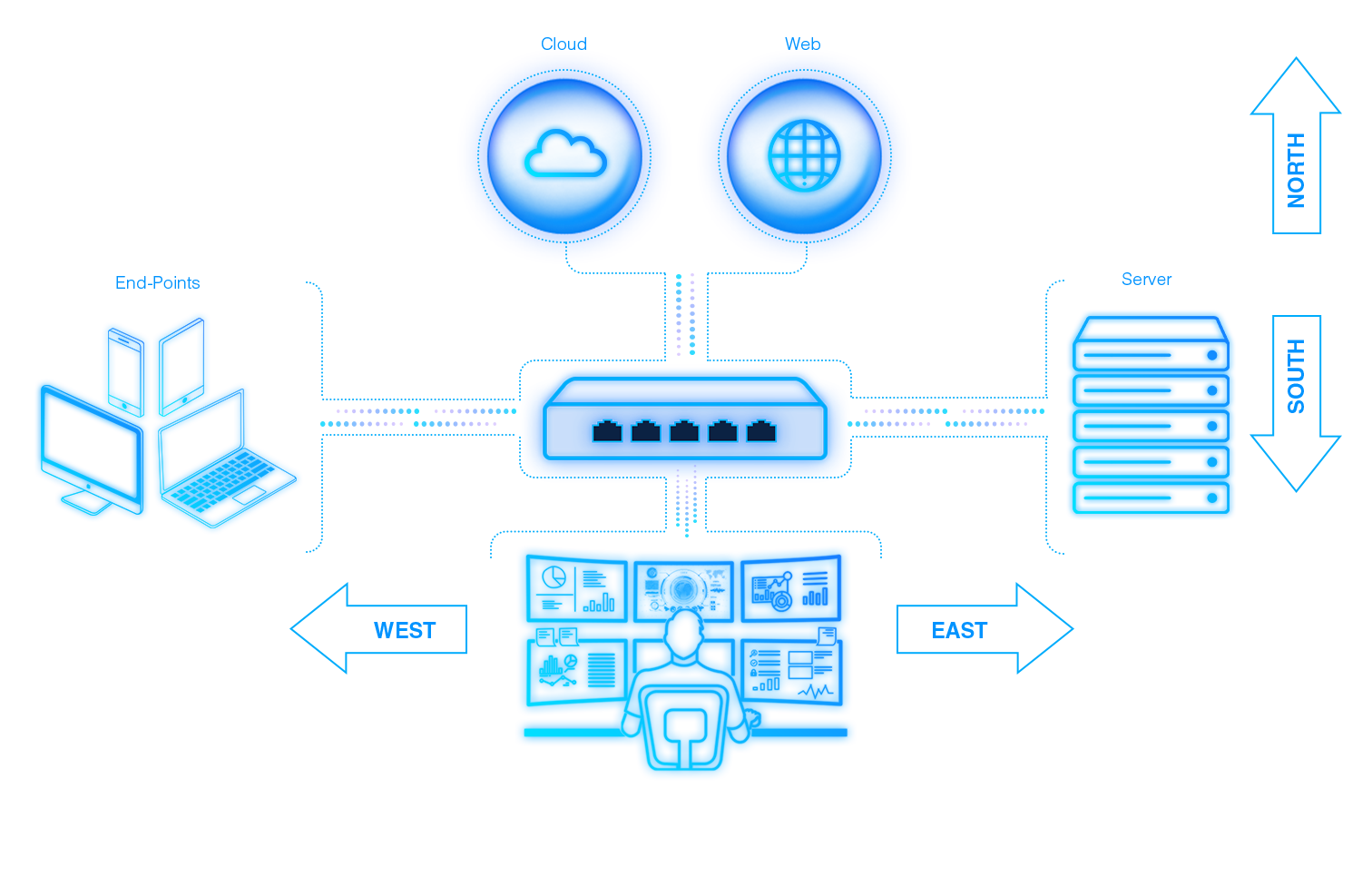

A Robust and Intelligent Service to Monitor & Protection of North-South & East-West Traffic
Holistic Protection Suite to Safeguard your Digital Assets from Modern-Day Threats
Robust IDS/IPS system leverages Artificial Intelligence and Machine Learning algorithms to detect and alert anomalies in network traffic. The advanced network behavior baselining is created to detect the deviations in case of DNS attacks, unauthorized scans and intruder actions. Signature-less detection protects the network from known and novel threats.
Integrated intelligence allows you to understand the threats in your network and easily prioritize responses with threat severity assessment. It eliminates guesswork so you can respond to threats decisively and automatically determines the scope and impact of threats found in the network.
The real-time monitoring system keeps vigil on north-south and east-west traffic to ensure protection from external and internal attacks. Our port level monitoring and control examines the lateral movement inside the network and blocks the unauthorized elements.
Monitoring of logs from perimeter devices like firewalls, routers, SD-WAN, etc. provides complete visibility on incoming and outgoing network traffic. Our intelligent alarm systems alert in case of a policy breach or hacking attempt.
Segmentation of network and workloads in cloud and data center environments provides a granular view of the secure zones and allows effective control. Our segment level security allows us to have better visibility and control over different fractions of the network and prevents collateral damage in case of a breach.
Our AI-driven approach to collect metadata and enrich it with intelligence helps to build automated response systems. The network behavior analytics provides inputs to create and deploy proactive control systems to limit the span of breach.
Complete visibility of data flow in external and internal networks
Artificial Intelligence for automation and real-time protection
Global Threat Graph access for forensics and breach analysis
Advance baselining for signature free protection to cover from novel threats
Based on Indicators of Attack (IOA) & Indicators of compromise to prevent targeted attacks
Micro-segmentation for granular visibility & control and to prevent collateral damage
Conclusive forensic investigations for proactive security

Blog

Do you ever wonder about the pre-built software in your computer? What will happen if it affects your security? What is the worst-case scenario? A pre-installed piece in your computer can pose a serious security risk [...]
Read MoreBlog

Citrix Systems, Inc. is an American multinational software company that provides server, application & desktop virtualization, networking, software as a service (SaaS), and cloud computing technologies [...]
Read MoreBlog

Technology is constantly evolving, and so is its relevance. In today’s world, its increasingly difficult to imagine a day without technology. Just think of the number of times that you rely on new age technologies for each activity [...]
Read More