Securing Assets - From Design To Deployment
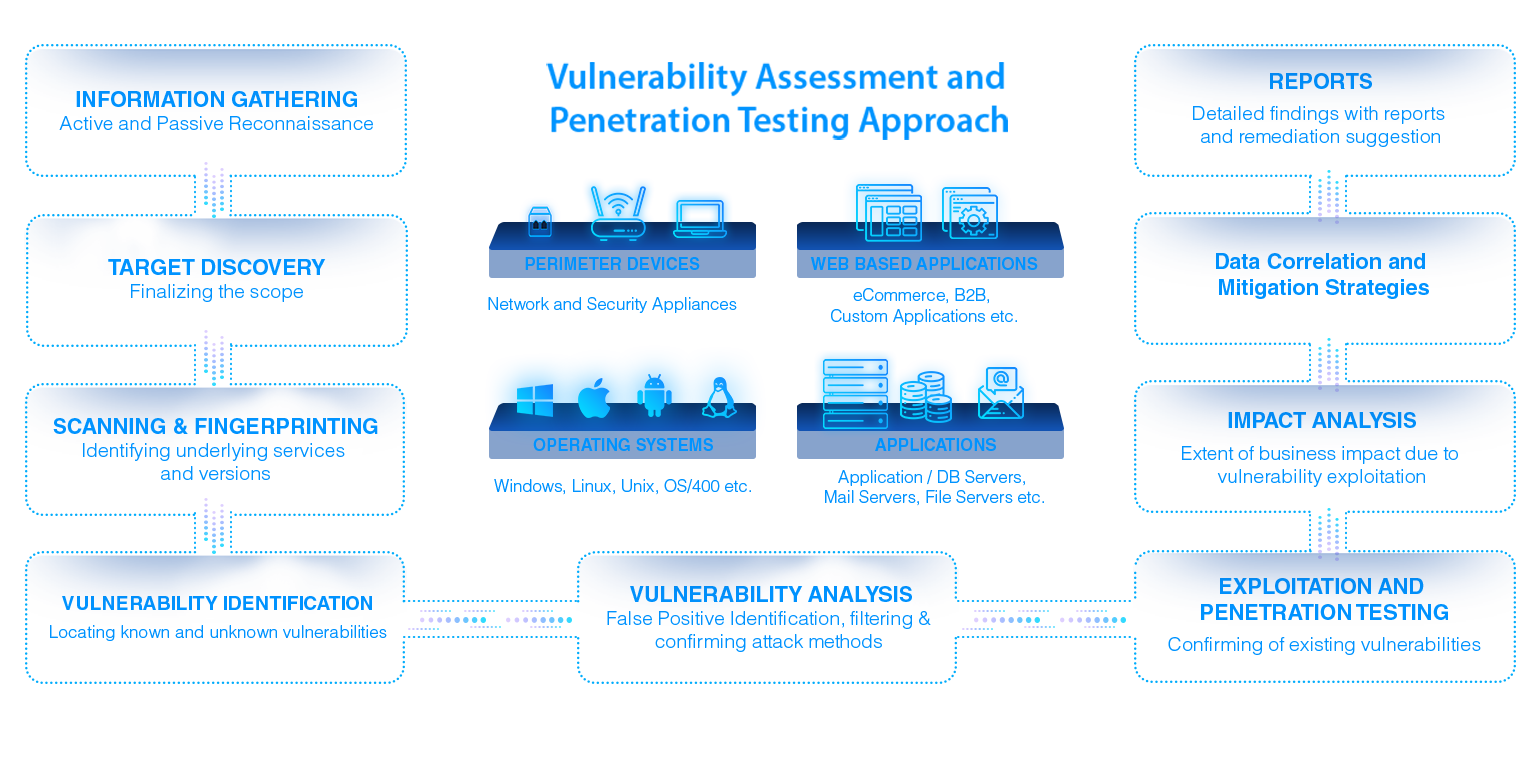
Our Vulnerability Assessment and Testing Service Defines, Identifies, Classifies, Prioritizes vulnerabilities, and Tests them in controlled environments. This Improves your proactive defense against Technological Vulnerabilities that can lead to Intrusions, Fraud, and Service Interruptions