
In the modern, technology-driven world, the term ‘hacking’ is rather associated with cyber threats and data breaches, ranging from individual gadgets to whole industries. Hacking, once a niche activity practiced by a few tech-savvy practitioners, has evolved into a global phenomenon that impacts businesses, governments, and individuals alike. The internet as well as the rise of new devices being connected have made it possible for hackers to exploit vulnerabilities to achieve their goals, whether for financial gain, political motives, or simply the thrill of disruption.
The fact about hacking is that it is not an easy thing to understand and therefore anyone who uses any digital gadget or is dependent on the internet should try as hard as possible to understand it. This blog delves into the evolution of hacking, exploring its history, the types of hacking, the tools hackers use, and the significant damage they can cause. Additionally, we’ll discuss how to guard against these threats and the role of ethical hacking in cybersecurity. At the end of this all-inclusive hacking guide, you will have a clearer understanding of possible hack scenarios and measures that can be taken to avoid the worst from happening.
What is Hacking? – Definition, Types, Security, and More
Cybercrimes can be defined as unauthorized attempt to access and/or control, modify or disrupt an asset of a computer system or network. While hacking is often associated with malicious activities, not all hacking is illegal or harmful. Hacking can be ethical, where security experts test systems to identify and fix vulnerabilities, or unethical where hackers aim to steal data, disrupt services, or cause damage. The core idea of hacking is to use one’s technical abilities to overcome these safeguarding mechanisms, including but not limited to passwords, encryptions, or some other form of protection to seize authority over digital assets.
Hacking can be broadly categorized into three main types: black hat, white hat, and grey hat hacking. Black hat hackers are those who use the skills for criminal purposes or unauthorized accesses, stealing sensitive data, spreading malware, or causing disruption. They often work anonymously and the motives are usually either based on profit or on the intention to causing harm. While there are the ‘black hat’ hackers who use his/her skills for ill errands, there are white hack hackers who use their skills for security enhancement. It is so frequently used for this purpose by organizations to scan systems for weaknesses to strengthen organization’s defence against threats. Others come in between, they are the so-called grey hat hackers; while they are unlikely to harm a system, they are also unlikely to have permission to probe for weaknesses in the system. Even though they do not aim to cause harm, their actions can still lead to unintended consequences.
There are a lot of consequences of hacking on individuals, businesses, and governments. Successful hacks result in the loss of data, money, the company’s reputation and in the worst-case scenario; national security issues. To the company, the breach can lead to customer estrangement, legal costs, and a recovery process that ends up being financially draining. On a larger scale, hacking can disrupt critical infrastructure, leading to widespread outages, or compromising sensitive information. The advancements in hacking techniques mean that even the most secure systems can be vulnerable, highlighting the importance of powerful cybersecurity measures.
Hacking is not just a technical challenge, it has become a significant social, economic, and political issue. The ethical debate surrounding hacking, especially regarding privacy and surveillance, continues to shape policies and laws globally. Understanding the nuances of hacking is essential for navigating the complexities of the digital world.
History of Hacking and Hackers
The origins of hacking can be traced back to the 1950s and 1960s when early computer enthusiasts began exploring the capabilities of computer systems. The first hackers were motivated by curiosity and a desire to push the boundaries of what was possible with technology. The first hack is said to have taken place at MIT, where students in the Tech Model Railroad Club began experimenting with the university’s mainframe computers. They applied what was known as ‘hacks’ to improve the performance and effectiveness of the system, thus giving rise to a hacking culture that was a result of exploration among other things. At this time, hacking was a noble objective as it was used to explore and experiment within the emerging field of computing.
Along with technology, the scope and impact of hacking also advanced. It was in the 1970s-80s that several high-profile hacks caught public attention. One such popular case involved Kevin Mitnick, a hacker who gained unauthorized access to dozens of systems, including those of major corporations and government agencies. This highlighted the vulnerabilities in early computer networks and led to his eventual arrest and imprisonment, making him a symbol of the dangers of hacking. Another notable event was the creation of the Morris Worm in 1988, one of the first computer worms to spread across the internet, causing widespread disruption and capturing attention to the need for stronger cybersecurity measures. These events marked the change from hacking being a niche activity to a significant concern for businesses and governments worldwide.
Like any other profession, hacking has transformed from a hobbyist pursuit to a highly organized and sophisticated activity. Today hackers come in all shapes and sizes, from those who act alone breaking into systems for personal profit to state-sponsored cybercriminals whose intention is neither patriotism nor profit-making but rather espionage and sabotage. The rise of the internet and the global interconnectedness of systems have expanded the reach and impact of hacking, making it a critical issue in the digital age. Modern hackers use advanced tools and techniques, often working in groups or networks to target a wide range of victims. That’s not all, for this evolution further highlights the progress that needs to be continuously made in cybersecurity to keep up with the ever-new threats emerging.
How Does Hacking Work?
Hacking involves various methodologies, each one exploiting different vulnerabilities in systems, networks, or devices. One common method is phishing where hackers use deceptive emails or websites to trick individuals into providing sensitive information such as passwords or credit card numbers. Malware is another widely used technique, where malicious software is installed on a victim’s device to steal data, monitor activities, or disrupt operations. Brute force attacks involve systematically trying different combinations of passwords until the correct one is found, often targeting accounts with weak security. Social engineering exploits human psychology rather than technical vulnerabilities, manipulating individuals into revealing confidential information. Each methodology requires a different skill set and is chosen based on the hacker’s goal and the target’s vulnerabilities.
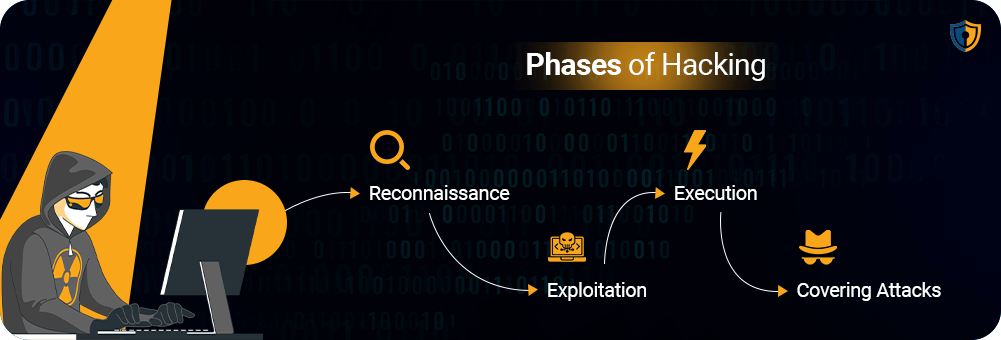
A typical hack goes through several phases, including reconnaissance, where the hacker gathers information about the target. This may be done by discovering possible entry points into the said system, studying their network, or probably even acquiring some personal information to aid in phishing attacks. The next stage is exploitation, where the hacker uses the information gathered to breach the target’s defences. This could involve deploying malware, exploiting software vulnerabilities, or using stolen credentials. Once inside the system, the hacker moves to execution, carrying out their intended actions, such as stealing data, installing additional malware, or disrupting operations. The final stage is covering attacks, where the hacker attempts to erase evidence of the breach to avoid detection. This might include deleting logs, using encryption, to hide stolen data, or creating false trails to mislead investigators.
Real-world hacking incidents demonstrate methods and stages of a hack. For example, in 2017, hackers exploited a known vulnerability in one of Equifax’s web applications. This provided an open door to sensitive data belonging to over 147 million people. Another famous case is the WannaCry ransomware attack in 2017, this was malware spread through emails in the form of a phishing message, which encrypted users’ data and then asked for money to release it. These examples show the devastating effect of hacking and, therefore, the importance of understanding how hackers operate to defend against such threats.
What Damage Can Hackers Do?
Probably, one of the most direct and acute effects of hacking is financial loss. Hackers can target either an individual by emptying their bank accounts or making fraudulent transactions, or an organization by causing extensive disturbances in operations that translate into lost revenues. Companies lose a lot from cyber-attacks because of finances, which translates to lost productivity, recovery time, and settlements with users. A good example of how hacking can result in financial loss is ransomware attacks. Here, hackers encrypt data that belongs to a victim by using malicious software. Besides the actual ransom, companies often must pay restoration costs in productivity, as well as possibly bearing the brunt of legal fees. However, the financial impact does not end with the directly connected losses; instead, it could even increase negative pressure from insurance premium increases, regulatory fines, and a decline in stock prices post-breach, which would only be further influenced following a high-profile incident.
Other major results of hacking include data breaches, which involve the theft of sensitive information like personal data, financial records, and intellectual property. The hackers either sell this information on the dark web or use it to attain targets of identity threats or as a means to further attack. The result of a data breach can be of enormous magnitude, affecting even millions of people, and may be detrimental in consequences to the organizations concerned in the long run. Customer data leakage has the potential to generate regulatory penalties, class-action lawsuits, and customer confidence impairments for businesses. Governments and public institutions are equally targetable in cases where a breach may reveal classified information or compromise national security. Of concern is that the rate and size of data breaches have increased in the recent past, placing the risk mitigation imperative on strong measures of data protection and strategies of cybersecurity.
In addition to the immediate financial and data losses, hacking can cause serious reputational harm to businesses and organizations. A well-publicized cyber hack can undermine customer trust, resulting in lost business and a damaged brand image. Restoring a reputation after a data breach or cyberattack is difficult and often demands considerable time and resources. Companies viewed as insecure or careless in safeguarding customer data may find it hard to keep and attract clients, which can ultimately affect profitability. In some instances, the reputational damage can be so extensive that it leads to the collapse of the company, particularly in fiercely competitive markets.
Hacking can also focus on essential infrastructure, including the power grid, transportation networks, and water supply systems. Cyberattacks on these vital areas can result in severe consequences, causing widespread disruptions, threatening public safety, and leading to economic chaos. The growing interconnectivity of critical infrastructure makes it an attractive target for state-sponsored hackers and terrorist groups.
Most Vulnerable Devices for Hacking

-
Smartphones
Smartphones are highly susceptible to hacking, primarily because of their widespread use and the extensive personal information they store. Hackers can take advantage of weaknesses in mobile operating systems, applications, or networks to access sensitive data like contacts, messages, and location details. Common hacking methods include phishing attacks, malicious applications, and insecure WiFi connections. Once a smartphone is compromised, it can be used to track the user’s activities, steal financial information, or even act as a gateway for larger attacks on connected devices and accounts. Additionally, the portability of smartphones heightens the risk of physical theft, which can lead to data breaches if the device isn’t properly secured.
-
Computers and Laptops
Due to their usage in private and business settings, computers and laptops are considered highly vulnerable to hacker attacks. These gadgets contain the users’ data, such as financial details, inventiveness, and passwords to almost all online platforms. Cyber terrorists can transfer viruses into a company’s computers through malware, phishing emails, or even by exploiting any vulnerability in the computer software system. Once inside, they install key loggers to capture passwords, use ransomware to lock files or gain control of the entire system. The rise of remote work has further increased the vulnerability of computers and laptops, as many employees access corporate networks from less secure environments at home, making them a potential entry point for cyberattacks.
-
IoT Devices
The recent growth of IoT gadgets including home appliances, security cameras and wearable technology exposes new risks. IoT appliances are not very secure today, leaving them vulnerable to being easily compromised by hackers. These gadgets are usually interfaced with home or corporate networks, meaning they can act as a haven for hackers. It becomes possible to carry out different malicious activities with the IoT device after it has been compromised for instant launching of Distributed Denial of Service (DDoS) attacks, spying on the users or even other devices on the same network. IoT has the problem of having no consistent security measures for any of the IoT-connected devices to make them secure from hackers.
-
Corporate Networks
Corporate networks are an attractive attract for hackers because they contain lots of important information and resources. Hackers find a loophole through weak access points, such as insecure devices or outdated software. Once inside they replace confidential information or interrupt normal operations or even use the breach to launch more attacks from other systems connected to the affected network.
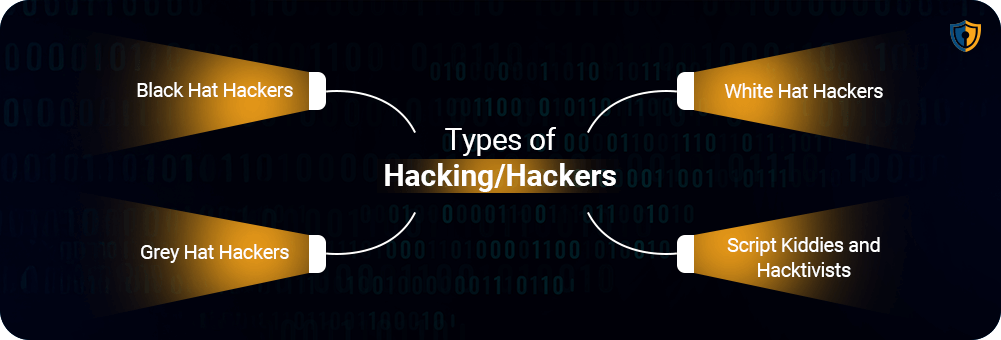
Types of Hacking/Hackers
-
Black Hat Hackers
A black hat hacker is a person who has the skill to illicit purposes for personal benefit mainly to inflict harm. Some of them are more selfish and criminal-minded and are out for the money or power and some just enjoy destruction for the sake of it. Black hat hackers are people who have specific technical ability to hack systems, networks and devices damaging them as much as possible. These hackers are the ones who have been conducting the most significant cyber-attacks that lead to data loss, financial losses, and operations disruptions. These activities are illegal and punishable by law, but many operate anonymously, making them difficult to apprehend.
-
White Hat Hackers
Ethical hackers or white-hat hackers use their talent to help the organization find and fix security vulnerabilities. Unlike black hat hackers, white hat hackers operate with the approval of the system owner and are normally hired by the companies to enact penetration tests and security. They are oriented towards enhancing the protection of systems and to prevent malicious attacks. White hat hackers are equally important as they aid organizations in detecting and predicting future possible threats by proactively identifying and addressing weaknesses in their defences. Their work is legal and highly valued in the cybersecurity industry.
-
Grey Hat Hackers
This type of hackers is found between the black hat and the white hat hackers, hence the name grey hat hackers. Although they exploit vulnerabilities without permission, their intent is not always malicious. The grey hat hackers work on their own and are responsible for identifying security weaknesses in organizations and reporting them to the said organizations and at times, they do this in the hope of being paid or being acknowledged. Still, they can perform illegal activities as they are not registered to be allowed to access the systems they breach into. Grey hat hackers usually work in shady areas meaning that while they do make a positive change, they are still technically breaking the law or ethical standards. Their motivations are diverse, ranging from curiosity to a desire to improve overall cybersecurity.
-
Script Kiddies and Hacktivists
Inexperienced hackers who rely on pre-written scripts or software created by others to carry out cyberattacks are called script kiddies. They generally lack the technical knowledge to develop their tools and are typically motivated by the desire to cause disruption or gain notoriety. While script kiddies may lack the skills of experienced hackers, they can still cause significant damage, especially when using powerful tools created by others.
Hacktivists on the other hand are hackers driven by political or social motives who use their skills to promote a cause or protest against perceived injustices. Their often targets are government agencies, corporations, or organizations they believe are engaging in unethical practices, looking to disrupt their operations or expose sensitive information to the public.
-
Organized Cybercrime Groups
A highly sophisticated and well-funded organizations that operate like traditional criminal enterprises are called organized cybercrime groups. These groups engage in large-scale cyberattacks, often targeting financial institutions, corporations, and government entities. Using advanced techniques and tools, they steal data, commit fraud, or launch ransomware attacks, posing a significant threat to global cybersecurity.
Hacking Tools
-
Malware
Malware, which stands for malicious software, is a common tool used by hackers to breach systems. It appears in various forms, such as viruses, worms, trojans, ransomware, spyware, and adware. Each type serves a distinct purpose, like stealing information, corrupting files, or gaining unauthorized access. For example, ransomware locks a victim’s files and demands a ransom for their release, while spyware quietly tracks user activities. Malware can spread through phishing emails, harmful websites, or infected software downloads. It represents a serious threat to both individuals and organizations by undermining data integrity, privacy, and security.
-
Phishing kits
Phishing kits are ready-made tools that let hackers create counterfeit websites or emails that closely resemble legitimate ones. These kits are designed to trick users into sharing sensitive information, such as login details, credit card information, or personal identification. They often come up with templates for well-known sites like banks, social media networks, and online shopping platforms, which enhances their effectiveness. With the emergence of phishing-as-a-service, even inexperienced hackers can launch phishing attacks without needing advanced technical knowledge. Phishing continues to be one of the most prevalent and successful methods of cyberattacks, as it takes advantage of human psychology and trust rather than exploiting technical weaknesses.
-
Keyloggers
Keyloggers are tools, either software or hardware, that are designed to secretly record the keystrokes made on a victim’s device. They are often used to capture sensitive information such as passwords, credit card numbers, and personal messages. Keyloggers can be delivered through malicious email attachments, software downloads, or even installed physically on a target computer. Once they are in place, they work quietly in the background, logging every keystroke and sending the information back to the hacker. The secretive nature of keyloggers makes them especially dangerous, as they can remain undetected for extended periods, enabling hackers to collect significant amounts of sensitive data over time.
-
DDoS Tools
Distributed Denial of Service (DDoS) tools are designed to flood a target website, server, or network with an overwhelming amount of traffic, making it impossible to use. Hackers frequently use these tools to interrupt business activities, harm reputations, or extort money in exchange for stopping the attack. Some well-known DDoS tools are LOIC, HOIC, and the Mirai botnet.
-
Penetration Testing Tools
Penetration testing tools such as Metasploit and Nmap are commonly utilized by both ethical hackers and cybercriminals to find and exploit system vulnerabilities. These tools assist hackers in mapping networks, identifying open ports, and evaluating potential weaknesses. Although they are intended for legitimate security assessments, they can also be misused for unauthorized hacking.
Prevention from Getting Hacked
-
Security Best Practices
Implementing strong security best practices is essential for defending against hackers. This involves using complex passwords that are changed regularly, avoiding the reuse of passwords across different platforms, and securing accounts with unique credentials. Keeping antivirus and anti-malware software installed and updated is crucial for detecting and removing potential threats. Enhancing network security can be achieved by using firewalls, securing Wi-Fi networks, and utilizing Virtual Private Networks (VPNs) for safe browsing. Organizations should enforce strict access controls to ensure that only authorized personnel can access sensitive data. Regular security audits and vulnerability assessments are also important for identifying weaknesses and strengthening defenses. Additionally, frequently backing up important data ensures that critical information can be recovered in the event of a breach.
-
Two-Factor Authentication
Two Factor Authentication (2FA) enhances the security of online accounts by requiring two different forms of verification. Usually, 2FA combines something the user knows, like a password, with something they possess, such as a mobile device or hardware token or something inherent to them, like biometrics (for example, a fingerprint). Even if a hacker manages to get hold of a password, 2FA greatly decreases the chances of unauthorized access. Many online services now provide 2FA options, including SMS codes, authenticator apps, or biometric verification. By adopting 2FA, both individuals and organizations can establish a strong defense against unauthorized access, thereby improving overall cybersecurity.
-
Encryption
Encryption transforms sensitive information into a format that cannot be easily read, preventing unauthorized access. Only individuals with the correct decryption key can retrieve the original data. This process is essential for safeguarding sensitive information, particularly when it is transmitted over the Internet. Organizations implement encryption to protect emails, financial transactions, and data stored on various servers and devices. Powerful encryption standards, like AES-256, are commonly used to defend against cyber threats. By encrypting their data, companies can ensure that even in the event of a security breach, the compromised information remains unreadable and unusable, greatly reducing the potential for harm.
-
Regular Updates and Patches
Regularly updating software and applying patches is crucial for ensuring cybersecurity. These updates typically fix newly identified vulnerabilities that hackers might take advantage of. By keeping operating systems, applications, and firmware current, both individuals and organizations can safeguard themselves against known threats and lower the chances of being exploited by cybercriminals.
-
Cybersecurity Awareness
Increasing cybersecurity awareness among employees and users is essential for preventing hacking attempts. Ongoing training programs can inform individuals about phishing, social engineering, and safe online habits. When people grasp the risks and identify potential threats, they are more prepared to prevent breaches and help maintain a secure digital landscape.
What is Ethical Hacking?
Ethical hacking, often referred to as penetration testing or white-hat hacking, is the practice of conducting authorized tests to assess the security of a system, network, or application. Ethical hackers employ the same methods and tools as malicious hackers, but they do so with the consent of the system owner to uncover vulnerabilities and weaknesses. The main objective of ethical hacking is to enhance security measures, thereby preventing potential cyberattacks and breaches. By proactively identifying and addressing risks, ethical hackers assist organizations in protecting sensitive data, maintaining trust, and adhering to regulatory standards, making them an essential part of contemporary cybersecurity strategies.
Role of Ethical Hackers
Ethical Hackers are essential for improving an organization’s cybersecurity by mimicking real-world attack scenarios. They perform a thorough evaluation of the organization’s digital infrastructure, pinpointing vulnerabilities that could be targeted by cybercriminals. After carrying out penetration tests, ethical hackers deliver detailed reports that highlight the weaknesses found, the potential consequences of those vulnerabilities, and suggested strategies for remediation. They also assist in establishing stronger defences, including advanced intrusion detection systems and enhanced security protocols. Essentially, ethical hackers act as a proactive defence mechanism, consistently testing and strengthening an organization’s cybersecurity efforts.
Legal Aspects
Ethical hacking is a legal practice that is frequently governed by a range of standards and guidelines, including the General Data Protection Regulation (GDPR) and the Payment Card Industry Data Security Standard (PCI DSS). Ethical hackers are required to obtain proper authorization and follow stringent ethical guidelines to ensure they do not violate legal boundaries or infringe on privacy laws.
Certification and Careers
Certifications such as Certified Ethical Hacker (CEH), Offensive Security Certified Professional (OSCP), and CompTIA PenTest+ validate the skills and knowledge of ethical hackers. These certifications are highly regarded in the cybersecurity field and can open doors to roles like penetration testers, security consultants, and cybersecurity analysts.
Case Studies
Several organizations have benefitted from ethical hacking. For example, Facebook runs a “Bug Bounty” program that rewards ethical hackers for finding vulnerabilities in their platform. Likewise, major financial institutions enlist ethical hackers to assess their security posture, proactively mitigating risks and maintaining customer trust.
Conclusion
The evolution of hacking mirrors our digital world’s strengths and weaknesses. As tech advances, so do hackers’ tactics. This ever-changing field requires us to shift our mindset from securing networks to staying vigilant, collaborating, and adapting our defences. We need to see hacking as a constant, widespread challenge, promoting a cyber awareness and resilience culture. It’s not just about tech solutions, we must also consider human factors, ethics, and proactive education. In a world where digital threats are always evolving, staying ahead requires vigilance, collaboration, and a proactive approach to cyber security. As we’ve seen throughout the evolution of hacking, the tactics used by cybercriminals are becoming increasingly sophisticated. It’s no longer enough to simply secure our networks, we must also be prepared to adapt our defences to counter emerging threats. G’secure Labs offer the industry’s best cybersecurity services to help you stay ahead of hackers and safeguard. Our team of experts can provide you with a comprehensive assessment of your security posture, identify vulnerabilities, and recommend tailored services to mitigate risks. Why wait until it’s too late? Contact G’secure Labs today for a free consultation and learn how we can help you build a powerful defence against cyber hacks.



